Microsoft Identiy Platform, Verification
Here are steps to be performed inorder to validate the Safran API and the Azure setup.
Precondition
It is assumed that the following steps has already be found working.
- It is assumed that you have set "SafranWebApiAuthenticationType": "None" in the appsettings.json file, as per the "No Authentifcation".
- Started IIS and used the Browse feature. Type /v1/version to complete the request. Note that databaselevel = -1 as we have not specified a database yet.
- Added ?connectionstringkey=<db alias> and observer that the connectionstring worked as intended and retrieves the databaselevel of your Safran database. Can be crosschecked by running the following command on the database specified in the connection string: select max(version_id) from version;
As this has already found to be working and that your Microsoft Identiy Platform on Azure is setup as well as your Safran API with the required information, you can use something like the Postman application to test your Safran API setup.
Set "SafranWebApiAuthenticationType": "jsonwebtoken" in the appsettings.json file and restart the Safran API in IIS.
Test 1
This test is using Postman. Start by running the following command:
“Get” Your Server IP or DNS:*Your Port*/v1/version
This verification does not require any database nor any Oauth Authorisation to pass the validation.
The expected response should look like this:
[
{
"apiName": "Safran.Project.Integration.API",
"apiDescription": "Safran Project Integration API",
"apiCopyright": "Copyright © 2024",
"apiCompany": "Safran Software Solutions AS",
"apiBuildDate": "2024-Jun-27",
"apiDllVersion": "8.0.0.0",
"apiFileVersion": "8.0.0.0",
"databaseVersion": "24.1.0.0",
"databaseLevel": -1,
"netFramworkVersion": "8.0.8 .NET 8.0.8"
}
]
Should the verification fail:
- Check ports
- Attempt to ping the server IP from your machine.
- Run nslookup from cmd.
- Verify that the API is installed correctly, by browsing the localhost from IIS on the Safran API server again.
Test 2
Test 2 is to verify the connectionstringkey, meaning that the connectionstring in the application.json is set up correctly.
It is the same query as in previous test, with a modification to the end. This test is using Postman.
“Get” Your Server IP or DNS:Your Port/v1/version?connectionstringkey=Your Database Alias
The expected response should look like this:
[
{
"apiName": "Safran.Project.Integration.API",
"apiDescription": "Safran Project Integration API",
"apiCopyright": "Copyright © 2024",
"apiCompany": "Safran Software Solutions AS",
"apiBuildDate": "2024-Jun-27",
"apiDllVersion": "8.0.0.0",
"apiFileVersion": "8.0.0.0",
"databaseVersion": "24.1.0.0",
"databaseLevel": 108,
"netFramworkVersion": "8.0.8 .NET 8.0.8"
}
]
Should the verification fail, there is probably an issue with your connectionstring.
- Check that you are able to ping the database from the WebServer.
- Check that the database alias matches what you use in your ConnectionStringKey
Test 3
As the previous verification passed the validation, the following will use the Microsoft Identity Platform.
On Azure in the "App registrations", navigate to the "Authorization" and populate the parameters as required. Most will be default and but some will require input.
This test is using Postman.
Populate Postman as follows on the "Auth" page:
Auth Type select value "OAuth 2.0".
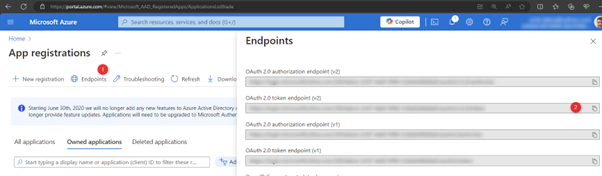
Access Token URL = Oauth 2.0 token endpoint (v2) from Azure, found in Home > App registrations, Endpoints:
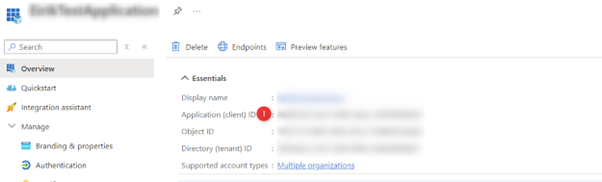
Client ID = Application (Client) ID from your Azure app reg.
Client secret = Your secret value generated earlier.
Scope = Application URI generated earlier, and set in application.json with the addition “/.default” parameter to the scope, for Postman.
In case using one App-registration to connect to another App-registration which hosts the Roles etc, one need to use the URI from the App-registration with roles etc. for this to work, as roles provided in the token will be based on this URI.
With everything properly populated, running the validation should be possible. it is assumed that the neccessary roles is granted in Azure.
Clicking the big orange button “Get new access token” within the Auth page of Postman.
- Authentication should complete without issues, if there are issues check the console of Postman to see what went wrong.
- Click Proceed then Use Token.
Validate Token
- Check the token to see that the roles associated are correct by used the JSON Web Tokens decrypter.
- Paste the token in the Encoded section to decrypt the token.
Validate a database request endpoint
- In case the role is configured to include “<db Alias>.all.read” Postman should be able to request any endpoint in the given database.
- Common test to run then:
- “Get": Your Server IP or DNS:Your Port/v1/project_previews?connectionstringkey=Your Database Alias
- “Get": Your Server IP or DNS:Your Port/v1/project_previews?connectionstringkey=Your Database Alias
If this validation fails, something is wrong with the setup of token. Please see Common Issues